
Problem 1
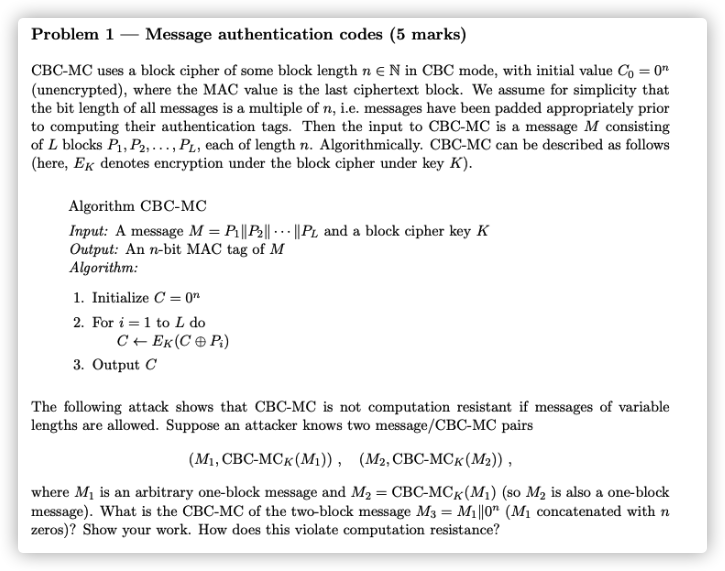
According to the encryption algorithm,we can get the ciphertext of M3 as follow:
C1=CBC−MCk(0n⊕M1)=M2C3=CBC−MCk(C1⊕0n)=CBC−MCk(M2)
It cannot play a role in increasing the difficulty of calculation because M3 is padded using 0n.
Problem 2

a.
According to the question,we get the information as follow:eAdA=1(mod p−1),eBdB=1(mod p−1)
We can compute MAdB as the next process:
MAdB=(CBdA)dB=CBdAdB=(CAeB)dAdB=CAdA=MeAdA=M(modp)
b.
Euler Theorem
c.
- eB will be computed when Eve hijacked the message CA and CB on the public communication channel. Then ,Eve will get dB according to eBdB=1(mod p−1).
- dA will be computed when Eve hijacked the message CB and MA on the public communication channel. Then ,Eve will get eA according to eAdA=1(mod p−1).
d.
The secret key is more shorter.
e.
The length of the plaintext of this algorithm has an upper bound.
Problem 3

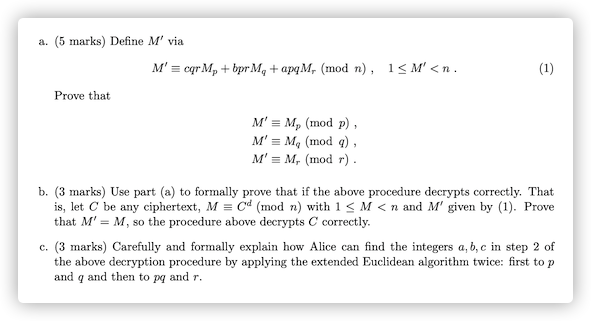
a.
According to cqr=1−bpr−apq, both sides of equation (1) take modulo p at the same time:
M′(modp)=(cqrMp+bprMq+apqMr+kn)(modp)=(cqrMp+bprMq+apqMr+kpqr)(modp)=cqrMp(modp)=(1−bpr−apq)Mp(modp)=Mp(modp)
Similarly, we can prove M′≡Mq(modq) and M′≡Mr(modr).
b.
According to Euler’s theorem:M(modp)=Cd(modp)=Cd(modφ(p))(modp)=Cdp(modp)=Mp(modp).
Similarly, we can get M(modq)=Mq(modq) and M(modr)=Mr(modr).
Those result are as follows:
⎩⎪⎨⎪⎧M≡Mp(mod p)M≡Mq(mod q)M≡Mr(mod r)
Let np=n/p=qr,nq=n/q=pr,nr=n/r=pq. Combining with apq+bpr+cqr=1,we can get np−1=c(modp),nq−1=b(modq),nr−1=a(modr).
To sum up,combining with the Chinese Remainder Theorem, we can see:
M=Mpnpnp−1+Mqnqnq−1+Mrnrnr−1(modn)=Mp(qr)c+Mq(pr)b+Mr(pq)a(modn)=cqrMp+bprMq+apqMr(modn)
That is, the above encryption is correct because we can get the proof of M′=M.
c.
- According to gcd(p,q)=1,∃x,y,s.t.xp+yq=1
- Easy to know gcd(pq,r)=1,∃s,t, s.t.s(pq)+tr=1
We do the following calculations:
1=s(pq)+tr=s(pq)+tr(xp+yq)=s(pq)+tx(pr)+ty(qr)
Then,a=s,b=tx,c=ty are the integers.
Problem 4

a:
According to the Jacobi symbol:
n=pq,→(nM)=(pM)(qM)
Because of gcd(e,φ(n))=1,we can infer that e is prime.
From the fact that both p and q are odd prime numbers:
- If M∣q or M∣p, we can get (0e=0), so the original formula clearly holds。
- If (pM)=−1,(qM)=−1,the original formula holds because of [(−1)(−1)]e=[(−1)(−1)].
- If (pM)=1,(qM)=−1,the original formula holds because of[(1)(−1)]e=[(1)(−1)].
- If (pM)=−1,(qM)=1,the original formula holds because of[(−1)(1)]e=[(−1)(1)].
- If (pM)=1,(qM)=1,the original formula holds because of[(1)(1)]e=[(1)(1)].
b:
According to C=Me+kn, we can prove as follow combining with the conclusion of (a):
(nC)=(nMe+kn)=(nMe)=(nM)e=(nM)
c:
RSA is not semantically secure:
Assuming we know the plain/ciphertext pairs,(M1,C1),(M2,C2), then we can forge information by setting M=M1M2.
We can get the ciphertext of M as follow:CM=(M1M2)e=M1eM2e=C1C2(modn)
Defeat polynomial security:
Suppose the adversary A randomly selects the quadratic non-residue r and m on modulo n:
- Let M0=rm,M1=M, and send them to the user.
- The user will select one of them and send its cipertext Mb to A.
- A will compute result=(nMb).If result=−1,M1 is encrypted,otherwise M0 is encrypted.
Proof as follows:
-
If M0 is encrypted,Mb=M0e(modn).
According to the result of (b),A can compute (nMb)=(nrm)=(nm)(nr)=(−1)(−1)=1
-
If M1 is encrypted,Mb=M1e(modn).
According to the result of (b),A can compute(nMb)=(nm)=−1
-
Adversary A can distinguish the source of the encrypted message every time, which is a polynomial security attack.
Problem 5

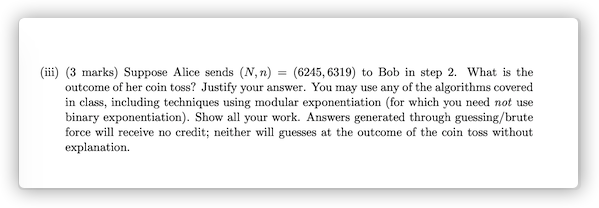
a.
Yes,because ∃r∈Zn∗,s.t.N=r2(modn)
b.
Proof by contradiction.
Assuming N=yr2(modn) is a quadratic residue,∃t∈Zn∗,s.t.t2=yr2(modn) will hold.
And then we can compute y because y=(tr−1)2(modn). We can get the conclusion that y is also a quadratic residue contrary to the statement of the question.
So N is a pseudosquare modulo n.
c.
- Bob will compute result=(pN) after receiving the p.
- If result=1,the outcome of Alice’s coin is “heads", if result=−1,the outcome is ”tails“.
d.
Determine whether N is a quadratic residue modulo n.
If N is a quadratic residue ,send “heads” to Alice,otherwise “tails”.
e.
1.p=71,q=89
(6319508)=(71508)(89508)=(7111+71∗7)(8989∗5+63)=(7111)(8963)
Compute (11/71) and (63/89) as follow:
(11/71)=−(5/11)=−(1/5)=−1
(63/89)=(26/63)=(13/63)=(11/13)=(2/11)=−(1/11)=−1
Because (6319508)=(−1)(−1)=1, 508 is a pseudosquare modulo 6319.
(63196245)=(716245)(896245)=(7168)(8915)
Compute (68/71) and (15/89) as follow:
(68/71)=(34/71)=(17/71)=(3/17)=(2/3)=−(1/3)=−1
(15/89)=(14/15)=(7/15)=−(1/7)=−1
Because (63196245)=(−1)(−1),the outcome of coin is “tails”.
Problem 6

a.
According to hz=x(modφ(p)),
so sh=ghz(modp)=gx(modp)=y(modp)
b.
Use the extend Euclidean algorithm to find the inverse of 17 modulo φ(p):
1=5−2∗2=7∗5−2∗17=7∗22−9∗17
so h−1=(−9)(mod22)=13.
According to hz=x(mod(p−1)):
we can compute z as z=xh−1(mod(p−1))=10∗13mod22=20
And then s=gz(modp)=520mod23=523−1∗5−2mod23=(25mod23)−1(mod23)=12
c.
s=y−h(modp)
Problem 7
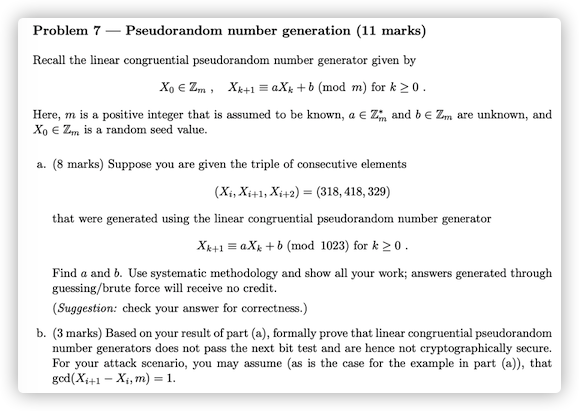
a.
Xi+1Xi+2≡aXi+b(mod m)≡aXi+1+b(mod m)
Easy to know:Xi+2−Xi+1=a(Xi+1−Xi)(modm),so we can get the information:−89=100a(mod1023),
Use the extend Euclidean algorithm to find the inverse of 100 modulo 1023:
1023100238=100∗10+23=23∗4+8=8∗2+7=7+1
So the follow will hold:
1=8−7=8∗3−23=100∗3−23∗13=100∗133−1023∗13
That’s mean 100−1=133(mod1023).
a=(−89)∗100−1(mod1023)=439(mod1023)
According to Xi+1=aXi+b(mod m):b=418−439∗318(mod1023)=967
Check the answer:
aXi+1+b=(439∗418+967)(mod1023)=429=Xi+2
b.
- According to the result of (a),the whole linear congruential pseudorandom number generator will be known easily if three consecutive numbers are acquired.
- The sequence period T is less than or equal to the modulo m.












